Learn: What is Cyber?
In this post, we talk about what is included in cybersecurity and define some common terms
Originally posted to a personal blog on Substack before transferring to this website.
While security is not a new concept, cybersecurity is fairly new
Security is not a new concept.
Lords and royalty in feudal societies built castles with drawbridges, ditches and moats to protect their keep. Governments keep security guards, armoured vehicles, and intelligence networks to protect their leaders and politicians.
The concept of cybersecurity is relatively new, having evolved only out of the more recent uptake of the internet and digital interactions. However, despite its more technical connotations (particularly when security specialists start discussing the use of encryption keys or Transport Layer Security protocols), cybersecurity draws from many of the learnings we developed from the physical security era of castles, guards and armoured vehicles.
In those circumstances, it can help to think about cybersecurity concepts in the physical space first, before turning to how they work in the digital.
Figure 1: Use of the words “cybersecurity”, “privacy” and “cyber”
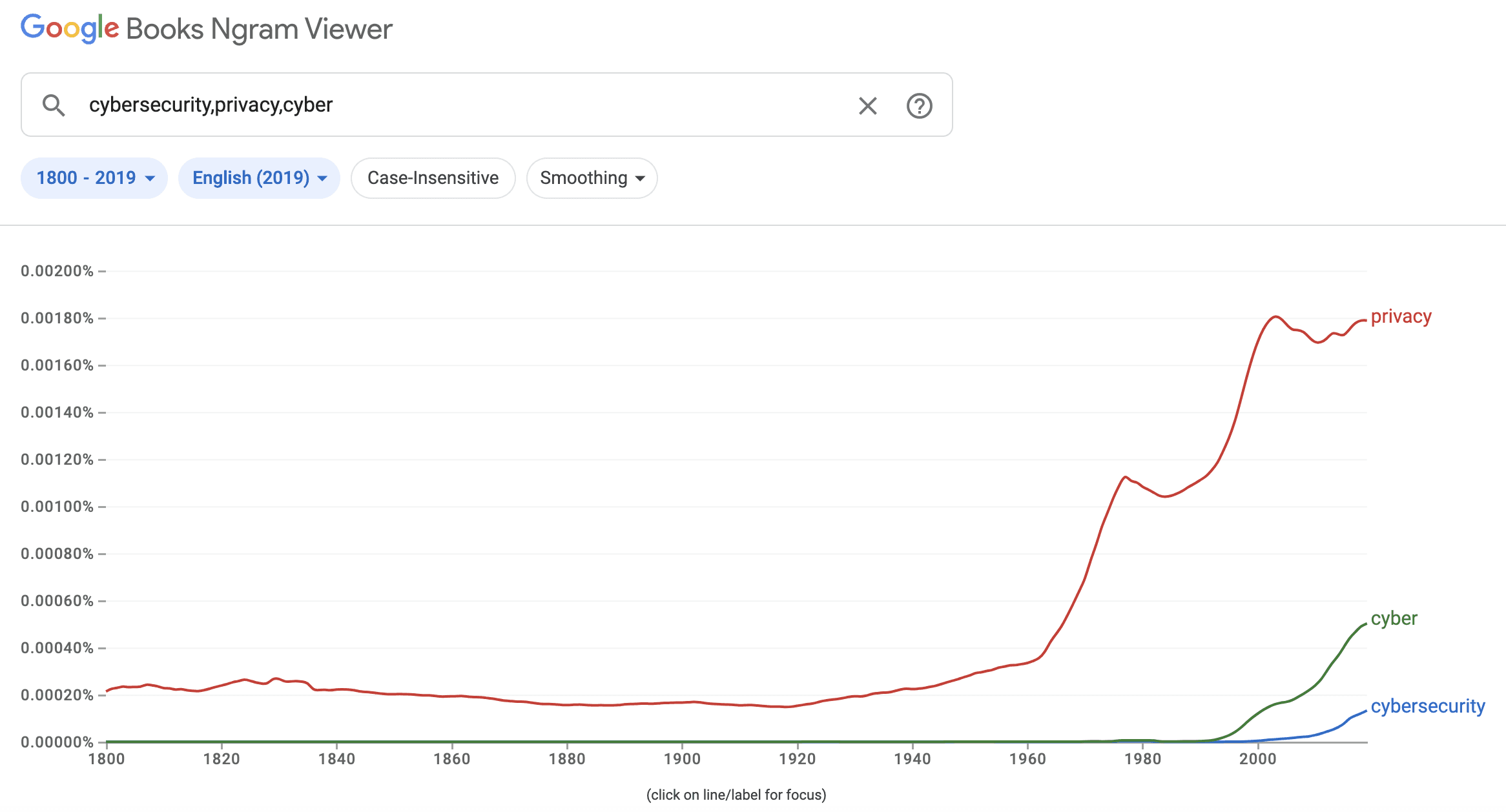
Notes: obtained on 3 March 2024 from Google Books Ngram Viewer
Generally, cybersecurity involves the protection of digital systems and information
There are many definitions of “cybersecurity”. This is unsurprising given how recently the use of the words “cyber” and “cybersecurity” has increased.
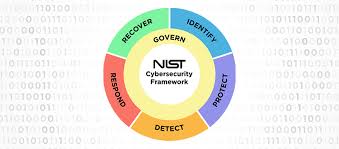
Nevertheless, a solid starting point is the National Institute of Standards and Technology (NIST), the US government agency promulgating cybersecurity standards, guidelines and best practices, including the most recent NIST Cybersecurity Framework 2.0 (CSF 2.0), released on 26 February 2024.
In general, NIST relies on a definition of “cybersecurity” that stems from a US Presidential Directive issued in 2008:
“cybersecurity” means prevention of damage to, protection of, and restoration of computers, electronic communication systems, electronic communication services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality and non-repudiation
While this is an absolute mouthful (and likely a byproduct of US political machinations), it is helpful to break this down into its two parts:
Digital Systems: ‘prevention of damage to, protection of, and restoration of [digital systems]’.
Information: **ensuring ‘availability, integrity, authentication, confidentiality and non-repudiation’ of information.
This definition means that cybersecurity is heavily interlinked (if not often encompassing) privacy and data protection
Given cybersecurity includes the protection of both digital systems and information, it is often understood in tandem with the more well-known and older concept of ‘privacy’ (see Figure 1).
More rigorous legislative regimes such as the GDPR (came into effect in 2018) and the CCPA (came into effect in 2020) have also resulted in the interchangeable use of the words ‘data protection’ or ‘information security’ **for the word ‘privacy’.
In the new CSF 2.0, NIST outlines the relationship between cybersecurity and privacy risks in a simplified Venn diagram (see Figure 2). It considers the two fields as distinct, but with significant overlap:
Cybersecurity risk management is essential for addressing privacy risks related to the loss of the confidentiality, integrity, and availability of individuals’ data. For example, data breaches could lead to identity theft. However, privacy risks can also arise by means that are unrelated to cybersecurity incidents.
For example:
If an employee of a large digital tech company starts using customer data to track that customer’s location on a 24/7 basis without the customer’s consent, then this would be a privacy incident but may not be a cybersecurity incident.
If a cybersecurity incident resulted in the downtime of a platform but no breach or other loss or alteration of information, then this would be a cybersecurity incident but may not be a privacy incident.
Figure 2: NIST CSF 2.0 cybersecurity and privacy risk relationship
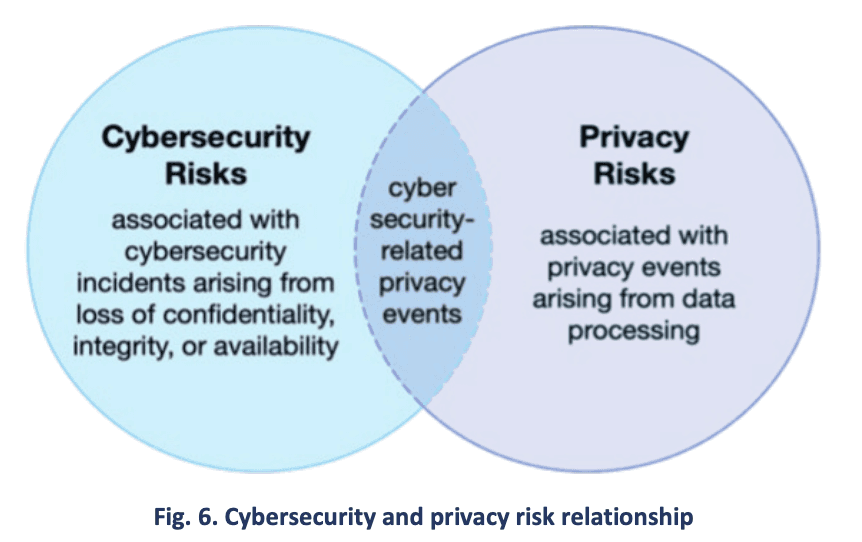
However, this distinction is not helpful when attempting to get a bird’s eye view over the risks that can arise in the digital space
From my perspective, this distinction is helpful when categorising incidents/risks and discussing the capabilities required to build and operate a successful team to help manage these new digital risks.
However, I personally don’t find this distinction to be helpful when looking at the space from the top-down. This is because:
When looking to prevent risks in this space, you want to be across all possible risks that could arise (cybersecurity, privacy and anything else that may not be captured by those definitions);
The distinction between cybersecurity and privacy leads to a siloing of skillsets between technical IT/cyber professionals and lawyers which detriments a team’s ability to manage the heavily intertwined nature of cybersecurity and privacy risks; and
The space is consistently changing which means that a definition formed in 2008 may no longer be relevant in 2024.
Indeed, just think about which of these you would care about more:
Loss of an essential digital service (eg, Google, online payments, online healthcare); or
Breach of sensitive personal information (eg, passwords, credit card details, medical history).
If the answer is that you care about both, then the conclusion is simple: we’ll need a way to be able to discuss the causes and impacts of both.
Conclusion: We'll generally define ‘cyber risk’ as encompassing all downside risk that can arise from the digital space (including both cybersecurity and privacy)
Our focus (stemming from the same approach undertaken by regulators under various data protection and cybersecurity legislation) will be on protecting individuals and entities from digital harm. This means we need to be able to examine and understand all types of harm that may arise from the digital space.
To avoid confusion between the various definitions that have been thrown into the ether, we will stick to these simplified definitions for the purposes of this blog:
Cyber: the digital space;
Cyber Risk: all downside risk that can arise from the digital space;
Cybersecurity: the protection of digital systems and information; and
Privacy (or Data Protection or Information Security): the protection of an individual’s (or entity’s) information from unauthorised use or disclosure.
But if you notice that I interchangeably use ‘cyber’ for ‘cyber risk’ or ‘cyber’ for ‘cybersecurity’, feel free to correct me. I’m always keen to hear feedback, questions and comments.